Share this
Tactical Edge Servers: Helping the Military Dominate the Battlespace
by Brett Daniel on Oct 30, 2020 4:25:27 PM
Graphic: Edge servers are at the epicenter of today's race to dominate the battlespace. Their usage at the tactical edge comes with numerous benefits that help the military accomplish this goal faster and more efficiently than its adversaries.
Table of Contents
- What is a tactical edge server?
- What are the benefits of deploying a tactical edge server?
- What are the defining features of a tactical edge server?
- What are some tactical edge server use cases?
- Conclusion: Choose Trenton for Tactical Edge Computing
Introduction
If you’ve been keeping up with military computing trends for the past three years or so, the concepts of cloud computing and edge computing have likely remained in your line of sight.
The United States Department of Defense (DoD) is leading multiple cloud computing endeavors, a portion of which involves migrating the computational power of the cloud data center to the tactical edge – that is, the place where combat, reconnaissance missions, and key decision-making are taking place.
But what exactly is the DoD aiming to accomplish by deploying tactical edge computing technologies?
In short, the Department is creating a unified, interconnected, situationally aware ecosystem – frequently referred to as the "internet of military things" or the "internet of battlefield things" - of proximal warfighters, commanding officers, aircrew, and other critical servicemembers across the branches of the military, further enabling the swift transfer of critical combat and mission data between each. This tactical edge collaboration provides the military with the geographical and computational wherewithal to take control of today’s increasingly data-driven battlespace, and keep adversaries deploying these same edge technologies at bay.
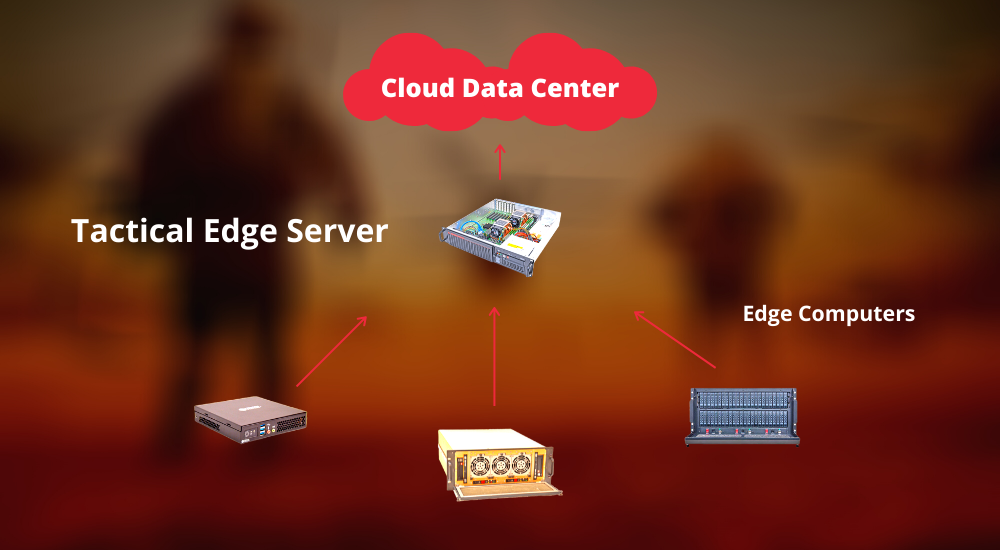
Edge servers, known as tactical edge servers when referring to edge servers deployed in the battlespace, are at the heart of the military’s collective adoption of edge computing technologies. Like any edge server, they’re the glue holding a series of data-generating clients and internet of things (IoT) devices together, but unlike just any edge server, they’re doing it on or near the battlefield, still using that same, beautifully efficient, divide-and-conquer edge computing architecture.
In this blog post, we’ll discuss why tactical edge servers are at the epicenter of future military edge computing applications, the benefits they offer, and present some use cases. At the end, we’ll tell you why you should put your trust in one of the leading, trusted tactical edge server manufacturers: Trenton Systems.

Photo: A ruggedized, sealed edge server manufactured by Trenton Systems
What is a tactical edge server?
A tactical edge server is a military computer deployed within the battlespace at or near sources of data-generating clients and devices. Tactical edge servers are almost always rugged or ultra-rugged, conforming to military and industrial standards, such as MIL-STD-810, DO-160, and MIL-S-901, depending on the conditions of the environment in which they’re deployed, and may include sealed chassis and conformal-coated motherboards.
These field-ready, true-grit edge servers can be installed on the battlefield quickly – in transit cases, forward operating bases (FOBs), ground control stations, and tactical cloudlets near data-capturing ground vehicles, aircraft, ships, and other sea vessels – all the while being utilized by troops and other key military personnel in the area.
Tactical edge servers send and receive enormous amounts of battlespace data collected by a variety of edge devices, mainly sensors, installed on unmanned aerial vehicles (UAVs), tanks and other military ground vehicles, and even on soldiers themselves.
In addition, tactical edge servers act as decentralized storage and application hubs for tactical edge warfighters using other rugged computing solutions in the field, such as rugged workstations, rugged mini PCs, and rugged storage systems. The key takeaway here is that tactical edge servers are providing computation where and while the action is taking place: within the battlespace and in real time.
The purpose of deploying tactical edge servers is simple: decentralize the processing power of the cloud data centers that military servicemembers rely on for computation. Just like other major businesses and organizations, the military also relies on far-flung data centers for computation and storage, but thanks to the tactical edge, this is changing, and for the better.
Graphic: The edge computing architecture, illustrated using rugged workstations and a rugged server manufactured by Trenton Systems
What are the benefits of deploying a tactical edge server?
Trenton Systems' Director of Engineering, Nate Young, offers some key insights on the benefits of tactical edge servers and edge computing.
The military sector greatly benefits from edge devices, like tactical edge servers, that can also function in harsh environments and climates. We call this tactical edge computing. The military can leverage this technology to provide troops in field with the fastest response times and reduced latency, even though they aren’t at HQ. This ensures that you have a protracted computational infrastructure for defense, no matter where the mission takes you. Now, your remote team can phone home in no time and acquire much-needed insight in real time.
So, we’ve addressed the technical reason as to why tactical edge servers are deployed: to decentralize the computational power of a cloud data center used by the military. But what real benefits do these edge networks offer?
There are four main benefits to deploying servers at the tactical edge:
- Latency reduction: Cloud data centers are often located thousands of miles away from the battlespace, creating a significant delay, or lag, in response times whenever data is requested by key military personnel in the field. By displacing some of the data center’s computational abilities, in this case, deploying a tactical edge server near the requestor, less data is sent to the cloud, reducing network latency and allowing troops to receive the information they need, faster. The same benefit applies to artificial intelligence systems and other edge devices in the field.
- Lots of money saved: Because data processing and storage is being handled by fielded tactical edge servers, less data is being transmitted to the cloud, allowing the military to save money on cloud computing costs. This money can then be allocated toward other projects, such as updating legacy computer systems.
- Faster decision-making: Because troops are experiencing reduced latency when phoning home, they can make strategic decisions faster. No more waiting for their requests to travel to the distant cloud data center. Tactical edge servers give the warfighter the information he or she needs to act with haste in the face of adversity, which, in some cases, translates directly into lives saved, and in all cases, makes for a more efficiently executed mission.
- Enhanced situational awareness: The battlespace of the future resembles something straight out of a science fiction movie: multiple autonomous systems, tanks, ground vehicles, aircraft, and warfighters transmitting data to each other in a digital cobweb of real-time warfare. This is possible but more difficult without edge computing technology. The improved common operating picture established as a result of tactical edge server deployment also improves overall situational awareness, as general surveying of the battlespace and its associated assets becomes easier and more accurate.
.png?width=1000&name=Untitled%20design%20(48).png)
Graphic: There are five defining features that comprise any worthwhile tactical edge server.
What are the defining features of a tactical edge server?
Some interesting trends in edge computing are geared towards the ruggedization of said edge devices. To successfully function in the field, the edge computer must be ready to tackle the environmental impacts first, then be ready to solve the task at hand faster, reliably, and for years to come. Here at Trenton Systems, rugged edge servers that will eventually be installed near, for example, unmanned aerial vehicles (UAVs), manned aircraft, tanks, armored vehicles, and other combat and reconnaissance assets, are being manufactured.
- Nate Young, Director of Engineering
The best tactical edge sever has six defining features:
- Rugged chassis and components
- SWaP-C-optimized configuration
- High-performance CPUs and RAM
- Lots of secondary storage
- Significant computer stress testing
- Cybersecurity protections
Rugged chassis and components
Ruggedizing tactical edge servers involves a few different manufacturing activities, depending on the specific program or application in or for which the server is being deployed. Mechanical shock and vibration testing in accordance with MIL-STD-810 is standard, given the frequent transportation of these systems and their situation in or near combat-heavy environments. The servers may also be temperature-tested to MIL-STD-810 for either end of the temperature spectrum - sub-zero temperatures for freezing environments, extremely high temperatures for dry, arid, sunlight-heavy environments, and even rapid fluctuations between each. High humidity is also a consideration. For further resistance to nature’s elements, chassis may also be sealed, and motherboards may also receive conformal coatings.
SWaP-C-optimized configuration
Optimizing the size, weight, and power (SWaP) of tactical edge servers is essential to ensure ease of transportability and scalability. The faster these servers can be deployed, the better. The less amount of space these servers take up, the more space available for other servers and devices. The "P" in SWaP may refer to either the power of the CPUs or power supply unit (PSU) wattage. For either case, there's a general focus on achieving adequate processing power and ensuring adequate wattage with which to handle the server's computational tasks. Cost (C) is all-encompassing: reduce costs as much as possible across the board, but don't sacrifice performance. The "C" may also refer to cooling, in which case the focus is on implementing fans or liquid cooling that prevent component overheating, and in turn, server failure.
Overall, with regard to SWaP-C, the general focus for military programs and applications is achieving a small-form-factor, lightweight tactical edge server with considerable compute power, adequate wattage, and adequate cooling, all at the lowest possible cost.
High-performance CPUs and RAM
Skimping on CPUs and RAM won’t win the race to dominate the battlespace. High-performance server motherboard CPUs, particularly Intel’s line of Xeon Scalable processors, and high-transfer-rate DDR4 RAM modules give your tactical edge server the brain power and short-term memory necessary to handle all those data-generating clients and devices in the field. If you’re running a lot of applications in real time, you’ll generally need more RAM to ensure performance consistency and prevent buffering or lag. Better CPUs improves the speed and efficiency at which these applications can operate.
Keep this short-and-simple quote by Intel in mind: “
More RAM is like a bigger workbench. A faster processor is similar to inviting a friend over to help you with your work.
Also, check out our Giant List of Intel’s Advanced Technologies, and always refer to Intel’s Product Specifications Database to ensure that your chosen CPUs have the advanced technologies you're looking for. You won't have to worry with that too much at Trenton Systems, as we take great in ensuring you have everything you need with regard to both CPUs and RAM.
To learn more about choosing between Xeon and Core CPUs for your server motherboard, check out Xeon vs. Core Processors: Choosing the Right Intel CPUs for Your Server Motherboard.
Lots of secondary storage
Don’t get so caught up in how quickly and efficiently your applications run while neglecting to provide adequate secondary storage in the form of high-capacity solid-state drives (SSDs) and hard disk drives (HDDs), particularly properly authenticated self-encrypting drives (SEDs) if you’re looking for a security boost as well. All that data generated in the field resides in RAM and will be lost the moment your system loses power; ergo, it’s important to ensure that you have enough secondary storage to save your most important data for future access. Nothing’s worse than realizing you don’t have enough drive capacity.
Ample computer stress testing
Maxing out the tactical edge server’s CPUs, GPUs, and RAM based on how the system will operate in the field is crucial to ensuring that the server doesn’t fail when you need it most. Computer stress testing assesses how the system responds to immense workloads, validating its operability, recoverability, and endurance when it’s exposed to lots of data generated from multiple applications running at once. There’s lots of software for computer stress testing, which we talk about in our Huge List of Computer Stress Test Software.
Cybersecurity protections
Cybersecurity may be the fifth defining feature of a tactical edge server, but it’s far from the least important. Operating system hardening – think Star Lab’s Titanium Security Suite – as well as hardware-based full disk encryption coupled with appropriate management solutions – think properly authenticated FIPS 140-2 storage drives coupled with FUTURA Cyber’s Drive Security Manager (DSM) – are just two of many important cybersecurity considerations for tactical edge servers. Without these and other standard protections like TPM 2.0, all that real-time data is exposed and ripe for adversarial access.

Photo: Transit case deployments are just one use case for tactical edge servers.
What are some tactical edge server use cases?
So, we’ve discussed what makes a tactical edge server and why they’re important for military programs and applications, but how are they actualized in the field?
Here are two common tactical edge server use cases:
- Servers installed in ground control stations for UAVs: Some ground control stations are transported to the area in which UAVs are operating. The UAV’s sensors are collecting a large amount of data that must be processed and stored somewhere, and when we’re talking UAV intelligence, surveillance, and reconnaissance, the less distance the data must travel, the better. Enter the nearby tactical edge server, helping the UAV and its operators stay in sync and on time.
- Servers installed in transit cases for in-field mobile deployments: Other rugged computing solutions and embedded edge devices collecting data where the action is taking place need a safe and secure hub for data processing and storage. Enter the tactical edge server housed in the classic, durable transit case, able to be moved about with ease no matter where the mission takes you.
- Servers installed in tactical cloudlets: Servers installed in tactical cloudlets offer an interesting use case. These are basically mobile data centers deployed at the edge that’s extending the computational power of the cloud, just like the singular tactical edge server. Nearby users can use these cloudlets to achieve low latency, faster decision-making, and enhanced situational awareness.
For more edge computing use cases, check out What Is Edge Computing [With Examples].

Photo: Choose Trenton Systems' made-in-USA rugged servers and workstations for your tactical edge deployments.
Conclusion: Choose Trenton for Tactical Edge Computing
To recap, a tactical edge server is a rugged military computer deployed at or near data sources within the battlespace. They offer four main benefits: latency reduction, reduction in cloud computing costs, faster decision-making, and enhanced situational awareness. Finally, the best tactical edge server has six defining features or characteristics: rugged chassis and components, a SWaP-optimized configuration, high-performance server CPUs and RAM, lots of storage drive capacity, stress-tested components, and critical cybersecurity protections.
Tactical edge servers are, and will continue to be, at the epicenter of the military’s tactical edge computing endeavors, especially as the DoD develops the JEDI Cloud, the cutting-edge enterprise cloud that will offer tactical edge capabilities to empower troops in the field.
Trenton Systems has already deployed custom and commercial off-the-shelf edge servers. We also strongly adhere to the six defining features of a worthwhile tactical edge server. Let us know how we can serve your military program or application today.
Share this
- High-performance computers (42)
- Military computers (38)
- Rugged computers (32)
- Cybersecurity (25)
- Industrial computers (25)
- Military servers (24)
- MIL-SPEC (20)
- Rugged servers (19)
- Press Release (17)
- Industrial servers (16)
- MIL-STD-810 (16)
- 5G Technology (14)
- Intel (13)
- Rack mount servers (12)
- processing (12)
- Computer hardware (11)
- Edge computing (11)
- Rugged workstations (11)
- Made in USA (10)
- Partnerships (9)
- Rugged computing (9)
- Sales, Marketing, and Business Development (9)
- Trenton Systems (9)
- networking (9)
- Peripheral Component Interconnect Express (PCIe) (7)
- Encryption (6)
- Federal Information Processing Standards (FIPS) (6)
- GPUs (6)
- IPU (6)
- Joint All-Domain Command and Control (JADC2) (6)
- Server motherboards (6)
- artificial intelligence (6)
- Computer stress tests (5)
- Cross domain solutions (5)
- Mission-critical servers (5)
- Rugged mini PCs (5)
- AI (4)
- BIOS (4)
- CPU (4)
- Defense (4)
- Military primes (4)
- Mission-critical systems (4)
- Platform Firmware Resilience (PFR) (4)
- Rugged blade servers (4)
- containerization (4)
- data protection (4)
- virtualization (4)
- Counterfeit electronic parts (3)
- DO-160 (3)
- Edge servers (3)
- Firmware (3)
- HPC (3)
- Just a Bunch of Disks (JBOD) (3)
- Leadership (3)
- Navy (3)
- O-RAN (3)
- RAID (3)
- RAM (3)
- Revision control (3)
- Ruggedization (3)
- SATCOM (3)
- Storage servers (3)
- Supply chain (3)
- Tactical Advanced Computer (TAC) (3)
- Wide-temp computers (3)
- computers made in the USA (3)
- data transfer (3)
- deep learning (3)
- embedded computers (3)
- embedded systems (3)
- firmware security (3)
- machine learning (3)
- Automatic test equipment (ATE) (2)
- C6ISR (2)
- COTS (2)
- COVID-19 (2)
- CPUs (2)
- Compliance (2)
- Compute Express Link (CXL) (2)
- Computer networking (2)
- Controlled Unclassified Information (CUI) (2)
- DDR (2)
- DDR4 (2)
- DPU (2)
- Dual CPU motherboards (2)
- EW (2)
- I/O (2)
- Military standards (2)
- NVIDIA (2)
- NVMe SSDs (2)
- PCIe (2)
- PCIe 4.0 (2)
- PCIe 5.0 (2)
- RAN (2)
- SIGINT (2)
- SWaP-C (2)
- Software Guard Extensions (SGX) (2)
- Submarines (2)
- Supply chain security (2)
- TAA compliance (2)
- airborne (2)
- as9100d (2)
- chassis (2)
- data diode (2)
- end-to-end solution (2)
- hardware security (2)
- hardware virtualization (2)
- integrated combat system (2)
- manufacturing reps (2)
- memory (2)
- mission computers (2)
- private 5G (2)
- protection (2)
- secure by design (2)
- small form factor (2)
- software security (2)
- vRAN (2)
- zero trust (2)
- zero trust architecture (2)
- 3U BAM Server (1)
- 4G (1)
- 4U (1)
- 5G Frequencies (1)
- 5G Frequency Bands (1)
- AI/ML/DL (1)
- Access CDS (1)
- Aegis Combat System (1)
- Armed Forces (1)
- Asymmetric encryption (1)
- C-RAN (1)
- COMINT (1)
- Cloud-based CDS (1)
- Coast Guard (1)
- Compliance testing (1)
- Computer life cycle (1)
- Containers (1)
- D-RAN (1)
- DART (1)
- DDR5 (1)
- DMEA (1)
- Data Center Modular Hardware System (DC-MHS) (1)
- Data Plane Development Kit (DPDK) (1)
- Defense Advanced Research Projects (DARP) (1)
- ELINT (1)
- EMI (1)
- EO/IR (1)
- Electromagnetic Interference (1)
- Electronic Warfare (EW) (1)
- FIPS 140-2 (1)
- FIPS 140-3 (1)
- Field Programmable Gate Array (FPGA) (1)
- Ground Control Stations (GCS) (1)
- Hardware-based CDS (1)
- Hybrid CDS (1)
- IES.5G (1)
- ION Mini PC (1)
- IP Ratings (1)
- IPMI (1)
- Industrial Internet of Things (IIoT) (1)
- Industry news (1)
- Integrated Base Defense (IBD) (1)
- LAN ports (1)
- LTE (1)
- Life cycle management (1)
- Lockheed Martin (1)
- MIL-S-901 (1)
- MIL-STD-167-1 (1)
- MIL-STD-461 (1)
- MIL-STD-464 (1)
- MOSA (1)
- Multi-Access Edge Computing (1)
- NASA (1)
- NIC (1)
- NIC Card (1)
- NVMe (1)
- O-RAN compliant (1)
- Oil and Gas (1)
- Open Compute Project (OCP) (1)
- OpenRAN (1)
- P4 (1)
- PCIe card (1)
- PCIe lane (1)
- PCIe slot (1)
- Precision timestamping (1)
- Product life cycle (1)
- ROM (1)
- Raytheon (1)
- Remotely piloted aircraft (RPA) (1)
- Rugged computing glossary (1)
- SEDs (1)
- SIM Card (1)
- Secure boot (1)
- Sensor Open Systems Architecture (SOSA) (1)
- Small form-factor pluggable (SFP) (1)
- Smart Edge (1)
- Smart NIC (1)
- SmartNIC (1)
- Software-based CDS (1)
- Symmetric encryption (1)
- System hardening (1)
- System hardening best practices (1)
- TME (1)
- Tech Partners (1)
- Total Memory Encryption (TME) (1)
- Transfer CDS (1)
- USB ports (1)
- VMEbus International Trade Association (VITA) (1)
- Vertical Lift Consortium (VLC) (1)
- Virtual machines (1)
- What are embedded systems? (1)
- Wired access backhaul (1)
- Wireless access backhaul (1)
- accredidation (1)
- aerospace (1)
- air gaps (1)
- airborne computers (1)
- asteroid (1)
- authentication (1)
- autonomous (1)
- certification (1)
- cognitive software-defined radios (CDRS) (1)
- command and control (C2) (1)
- communications (1)
- cores (1)
- custom (1)
- customer service (1)
- customer support (1)
- data linking (1)
- data recording (1)
- ethernet (1)
- full disk encryption (1)
- hardware monitoring (1)
- heat sink (1)
- hypervisor (1)
- in-house technical support (1)
- input (1)
- integrated edge solution (1)
- international business (1)
- licensed spectrum (1)
- liquid cooling (1)
- mCOTS (1)
- microelectronics (1)
- missile defense (1)
- mixed criticality (1)
- moving (1)
- multi-factor authentication (1)
- network slicing (1)
- neural networks (1)
- new headquarters (1)
- next generation interceptor (1)
- non-volatile memory (1)
- operating system (1)
- output (1)
- outsourced technical support (1)
- post-boot (1)
- pre-boot (1)
- private networks (1)
- public networks (1)
- radio access network (RAN) (1)
- reconnaissance (1)
- rugged memory (1)
- secure flash (1)
- security (1)
- self-encrypting drives (SEDs) (1)
- sff (1)
- software (1)
- software-defined radios (SDRs) (1)
- speeds and feeds (1)
- standalone (1)
- storage (1)
- systems (1)
- tactical wide area networks (1)
- technical support (1)
- technology (1)
- third-party motherboards (1)
- troposcatter communication (1)
- unlicensed spectrum (1)
- volatile memory (1)
- vpx (1)
- zero trust network (1)
- January 2025 (1)
- November 2024 (1)
- October 2024 (1)
- August 2024 (1)
- July 2024 (1)
- May 2024 (1)
- April 2024 (3)
- February 2024 (1)
- November 2023 (1)
- October 2023 (1)
- July 2023 (1)
- June 2023 (3)
- May 2023 (7)
- April 2023 (5)
- March 2023 (7)
- December 2022 (2)
- November 2022 (6)
- October 2022 (7)
- September 2022 (8)
- August 2022 (3)
- July 2022 (4)
- June 2022 (13)
- May 2022 (10)
- April 2022 (4)
- March 2022 (11)
- February 2022 (4)
- January 2022 (4)
- December 2021 (1)
- November 2021 (4)
- September 2021 (2)
- August 2021 (1)
- July 2021 (2)
- June 2021 (3)
- May 2021 (4)
- April 2021 (3)
- March 2021 (3)
- February 2021 (8)
- January 2021 (4)
- December 2020 (5)
- November 2020 (5)
- October 2020 (4)
- September 2020 (4)
- August 2020 (6)
- July 2020 (9)
- June 2020 (11)
- May 2020 (13)
- April 2020 (8)
- February 2020 (1)
- January 2020 (1)
- October 2019 (1)
- August 2019 (2)
- July 2019 (2)
- March 2019 (1)
- January 2019 (2)
- December 2018 (1)
- November 2018 (2)
- October 2018 (5)
- September 2018 (3)
- July 2018 (1)
- April 2018 (2)
- March 2018 (1)
- February 2018 (9)
- January 2018 (27)
- December 2017 (1)
- November 2017 (2)
- October 2017 (3)
/Trenton%20Systems%20Circular%20Logo-3.png?width=50&height=50&name=Trenton%20Systems%20Circular%20Logo-3.png)
.png?width=1000&name=Untitled%20design%20(47).png)


No Comments Yet
Let us know what you think