Zscaler® Internet Access
Cloud-based secure web gateway that inspects all inbound and outbound internet traffic, providing advanced threat protection and secure internet access.
Zscaler® Private Access
Secure connections between devices and network resources, regardless of device or location, to ensure only authenticated and authorized users can access sensitive information and resources.
Cloud-based, true zero trust cybersecurity technologies from Zscaler®
Zscaler-protected solutions

BAM Servers
Enhanced compute and connectivity secured by zero trust protections.
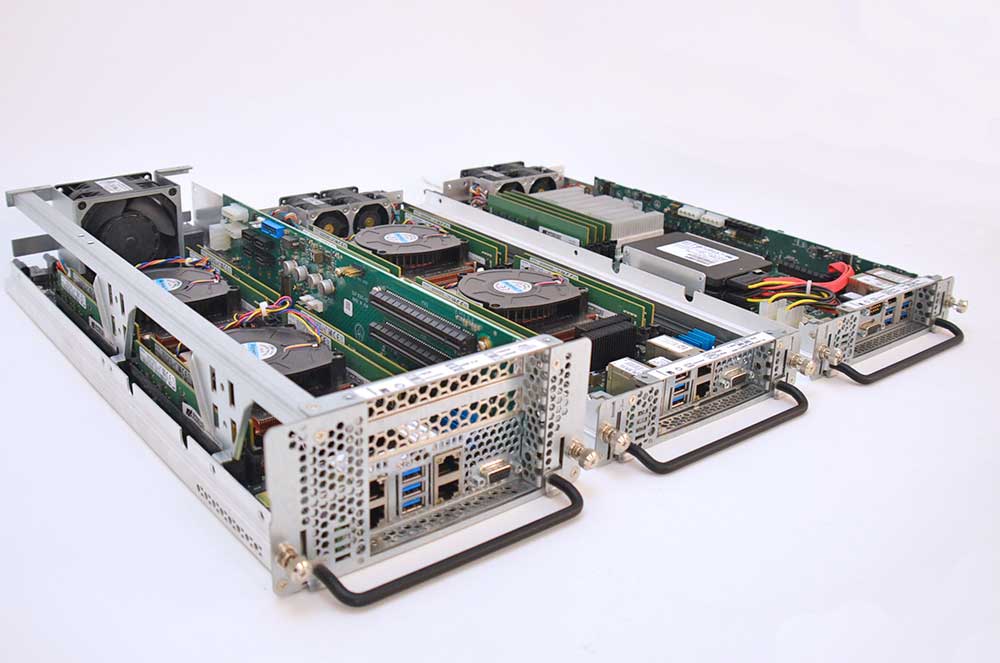
Blade Servers
Guard multiple critical workloads within compact enclosures.

3PI Servers
Accelerate time to market with servers supporting third-party motherboards.

Secure internet access
Internet connections encrypting data in transit and providing granular control over web traffic to reduce the risk of data breaches.
Secure access anywhere, anytime
Authorized users can securely access critical resources, applications, and data from any device or location and maintain collaboration.Trenton Systems Solutions Protected by Zscaler®
Custom, zero-trust architected solutions per your most complex requirements.

Advanced Protection
Real-time threat intelligence, sandboxing, and machine learning algorithms to limit physical and digital attack surface.

Strict Access Control
Ensuring users only access resources and data they are authorized to access to contain any potential security incidents.
/Trenton%20Systems%20Circular%20Logo-3.png?width=50&height=50&name=Trenton%20Systems%20Circular%20Logo-3.png)